You will not be able to change the package after this!
Are you sure you want to unlock

You will not be able to change the package after this!
Are you sure you want to unlock


Unlock a vast assortment of test series covering the most competitive exams in India to advance your career. All of this is free!
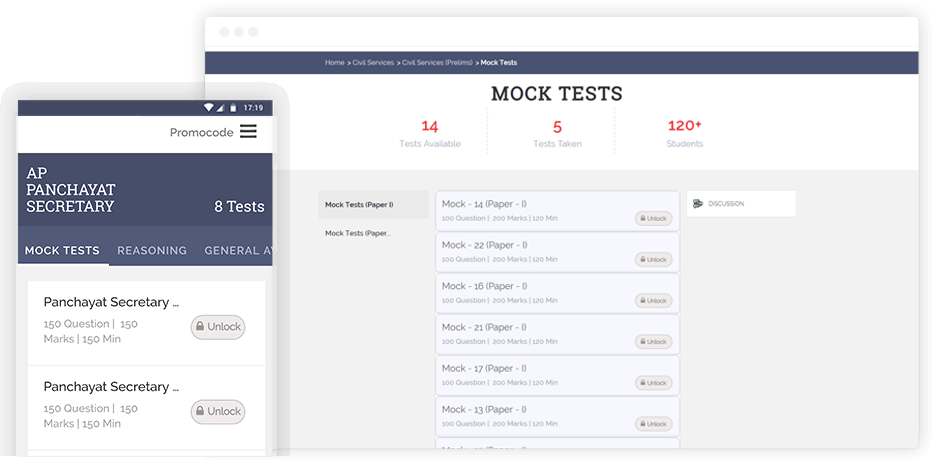
Not only right responses obtain a thorough explanation for each inquiry. You can practice your weak areas and retake the tests. Furthermore, you will have a forum to debate all the common questions on our interactive forum.
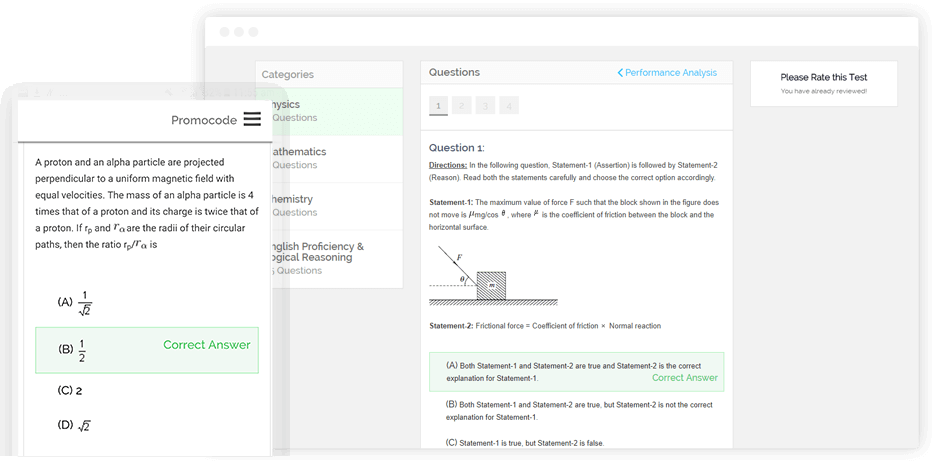
We think that hitting your target is equally as important as aiming. For this reason, we offer the highest caliber assessments, carefully created and evaluated by IIT-IIM alumni.
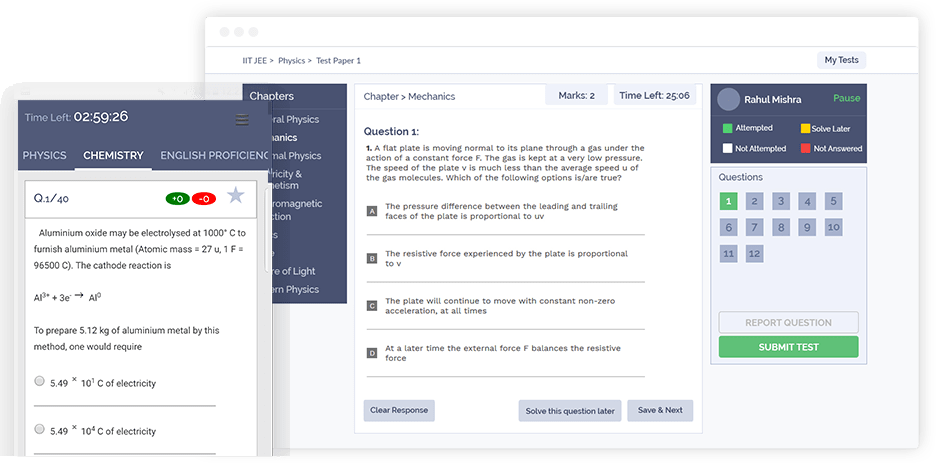
One Stop Solution
For All Exam Preparation and Online Learning
Live classes, Mock Tests, Videos and eBooks in one package

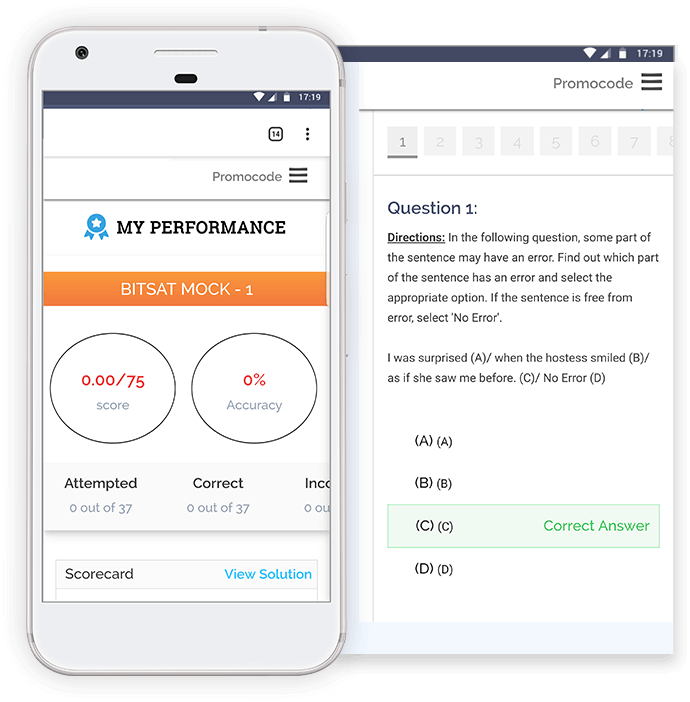
Obtain Personalized Learning Outcomes. a thorough performance analysis that reveals your areas of strength and weakness as well as your state, national, and overall rankings. A virtual tutor who is totally committed to helping you reach your full potential will also be provided to you. Using machine learning, it will rank your concepts, chapters, themes, and questions in order of importance. Exclusively on the F5 GURU Test Series, get this cutting-edge educational experience!